Introduction
Kerberos, named after the mythical three-headed dog guarding the gates of the underworld, is a security protocol that enables secure authentication in network environments. It offers a significant improvement over older protocols like NTLM by allowing the delegation of credentials across multiple machines, making it ideal for distributed computing environments.
Key Features of Kerberos
One of Kerberos’ primary security enhancements is its use of encrypted tickets for authentication rather than password-based exchanges. This reduces the risk of credentials being intercepted during transmission, significantly enhancing security.
Another important feature is credential delegation. This allows credentials to be securely passed across multiple machines, which is essential when users need to access resources from different systems or services.
How Kerberos Authentication Works
In a Kerberos-based authentication process, several key players are involved: the client, the server, and the domain controller, typically Active Directory (AD). Here’s a simplified overview of how the authentication process works:
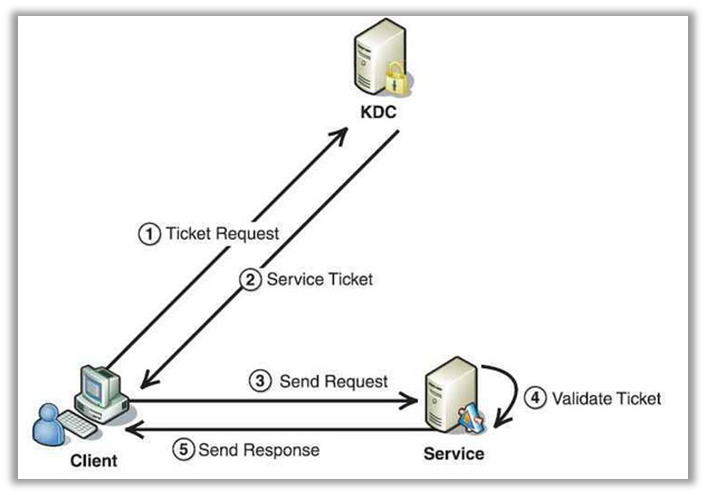
- After the user has logged into windows and received the Ticket Granting Ticket (TGT), it passes the TGT to the domain controller to request a Service Ticket. The service ticket is granted based on the Service Principal name. The SPN is for a specific service type and host name. With SQL Server, the port number or instance name is also included.
- If Active Directory locates the SPN, it returns the Service Ticket to the client.
- The client logs into the server and presents the Service Ticket as proof of identity.
- The service decrypts the ticket based on its service account. If the decryption succeeds, then it can validate the user identity. If it fails, the login is rejected.
- The server responds with data (HTML) or that the login succeeded (SQL).
Kerberos Delegation
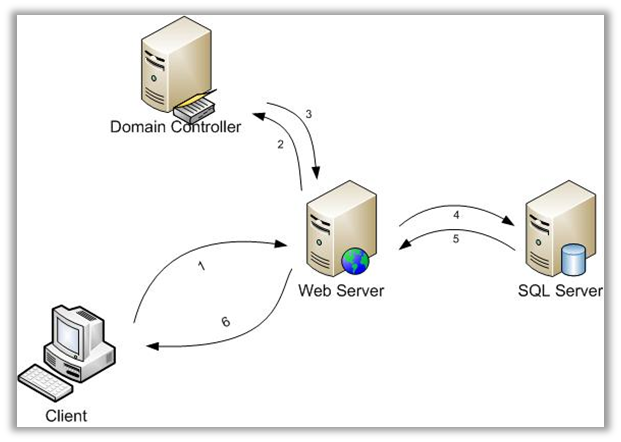
- The client passes the Service Ticket and Ticket Granting Ticket to the server. The server decrypts the Service Ticket and validates the user’s identity.
- The service needs to delegate the user’s credentials to SQL Server, so it passes the TGT to Active Directory and asks for a Service Ticket for SQL Server on the user’s behalf.
- The domain controller returns a new Service Ticket.
- The web server connects to SQL Server and passes the Service Ticket to SQL Server as part of the login process.
- SQL Server decrypts the Service Ticket and validates the user identity.
The Double Hop Scenario
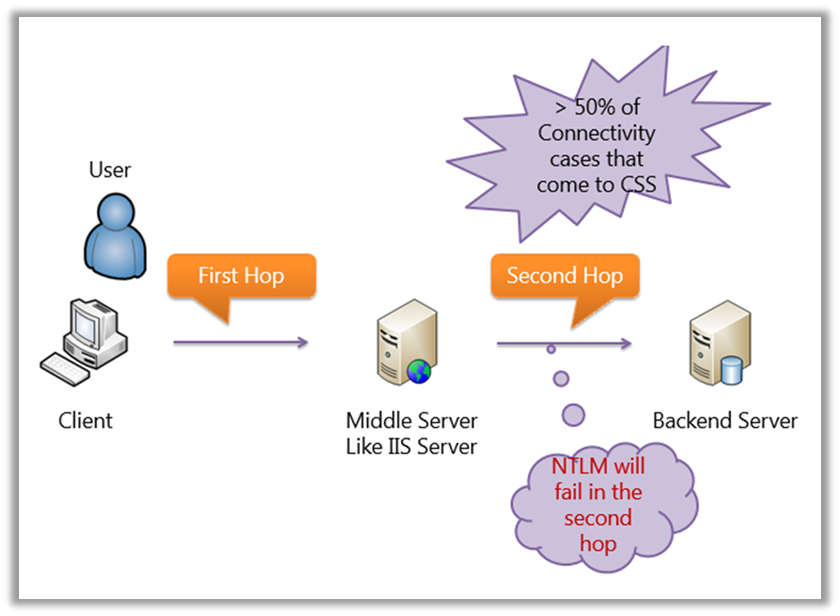
- The client provides credentials to the domain controller, which returns a Kerberos Ticket Granting Ticket (TGT).
- The client uses the TGT to request a service ticket for Server 1.
- The client connects to Server 1, providing both the TGT and the service ticket.
- Server 1 uses the client’s TGT to request a service ticket for Server 2.
- Server 1 then connects to Server 2 using the client’s credentials.
Common Issues with Kerberos Authentication
While Kerberos offers robust security, configuring it can be challenging. Below are some common issues administrators may encounter:
- Missing or Misconfigured SPNs (Service Principal Names): If an SPN is not registered or is registered to the wrong account, authentication will fail.
- Duplicate SPNs: When an SPN is associated with multiple accounts, Kerberos cannot determine which account to use, resulting in authentication failure.
- Clock Skew: Kerberos is sensitive to time discrepancies between the client, server, and AD. Even small differences in system clocks can cause authentication to fail.
Additionally, if the service account is a user account, the delegation tab may be missing until a service principal name is registered for the account. Without this, constrained delegation cannot be set up.
To Debug you can use SQLcheck found here SQLCHECK · microsoft/CSS_SQL_Networking_Tools Wiki (github.com)
Conclusion
Kerberos remains a powerful and secure authentication protocol, essential for managing access across distributed systems. Its ability to use encrypted tickets and support credential delegation makes it a significant improvement over older protocols like NTLM. However, proper configuration is key to ensuring that Kerberos operates smoothly, as issues such as misconfigured SPNs or time discrepancies can hinder its effectiveness. By understanding the fundamental workings of Kerberos and being aware of potential pitfalls, administrators can better leverage its strengths to enhance security and streamline authentication processes within their networks.